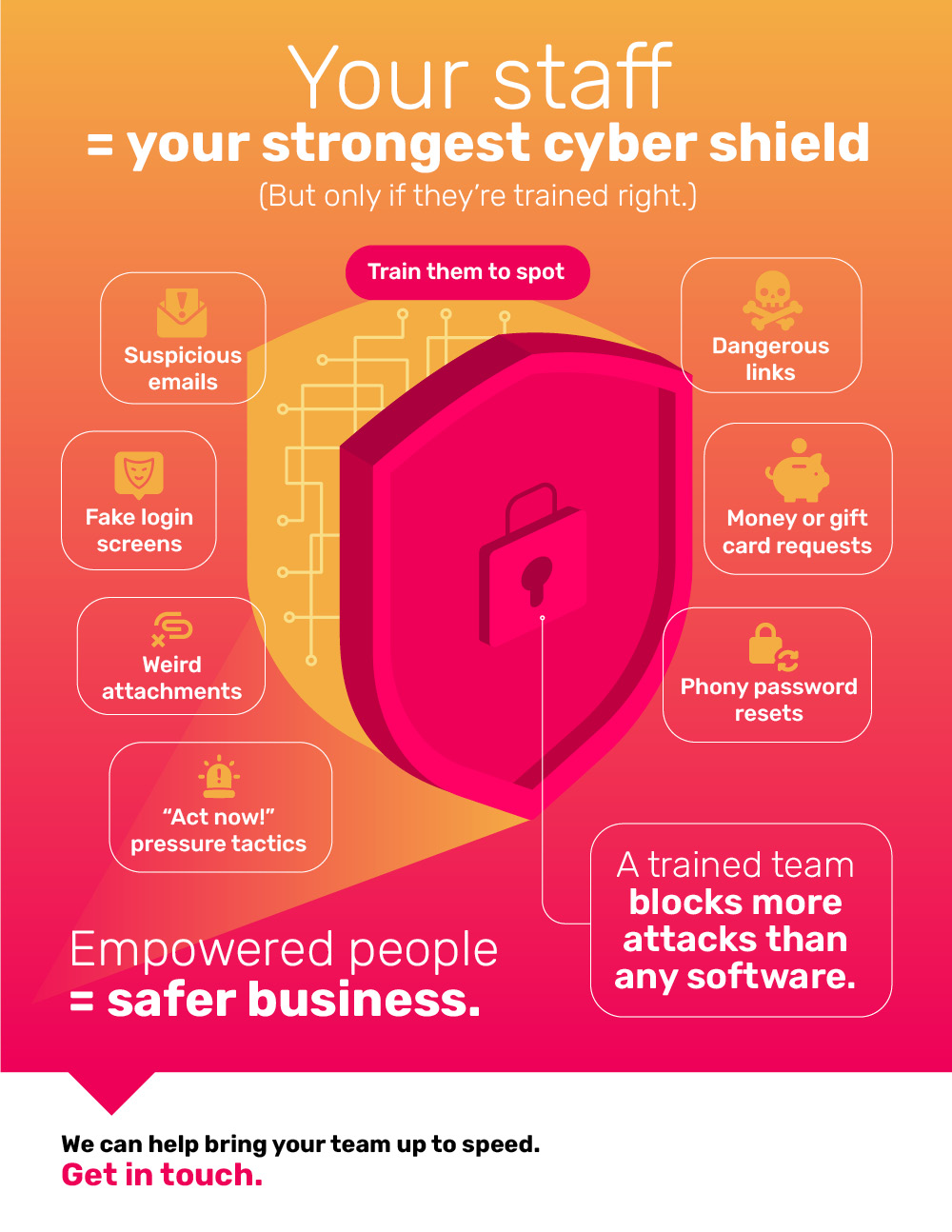
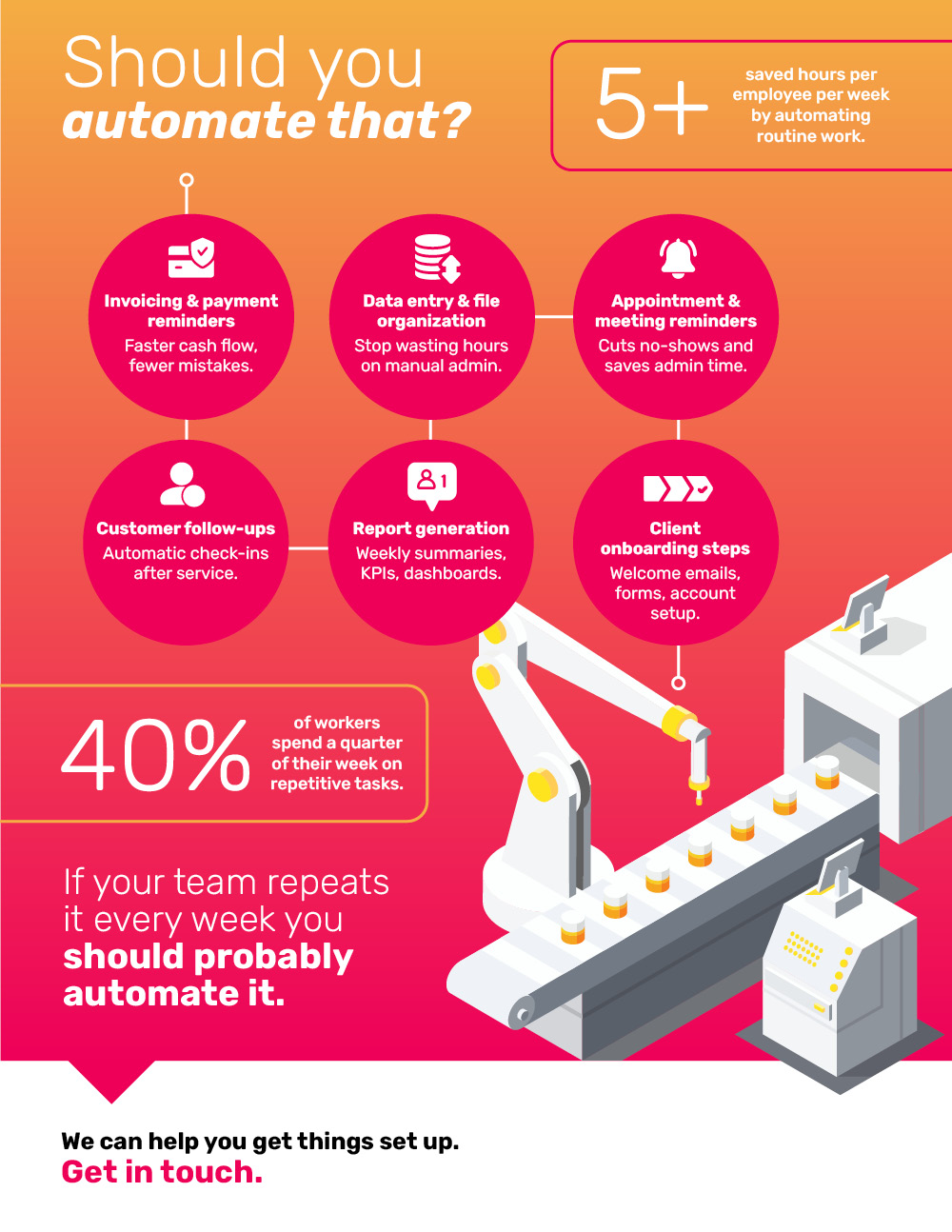
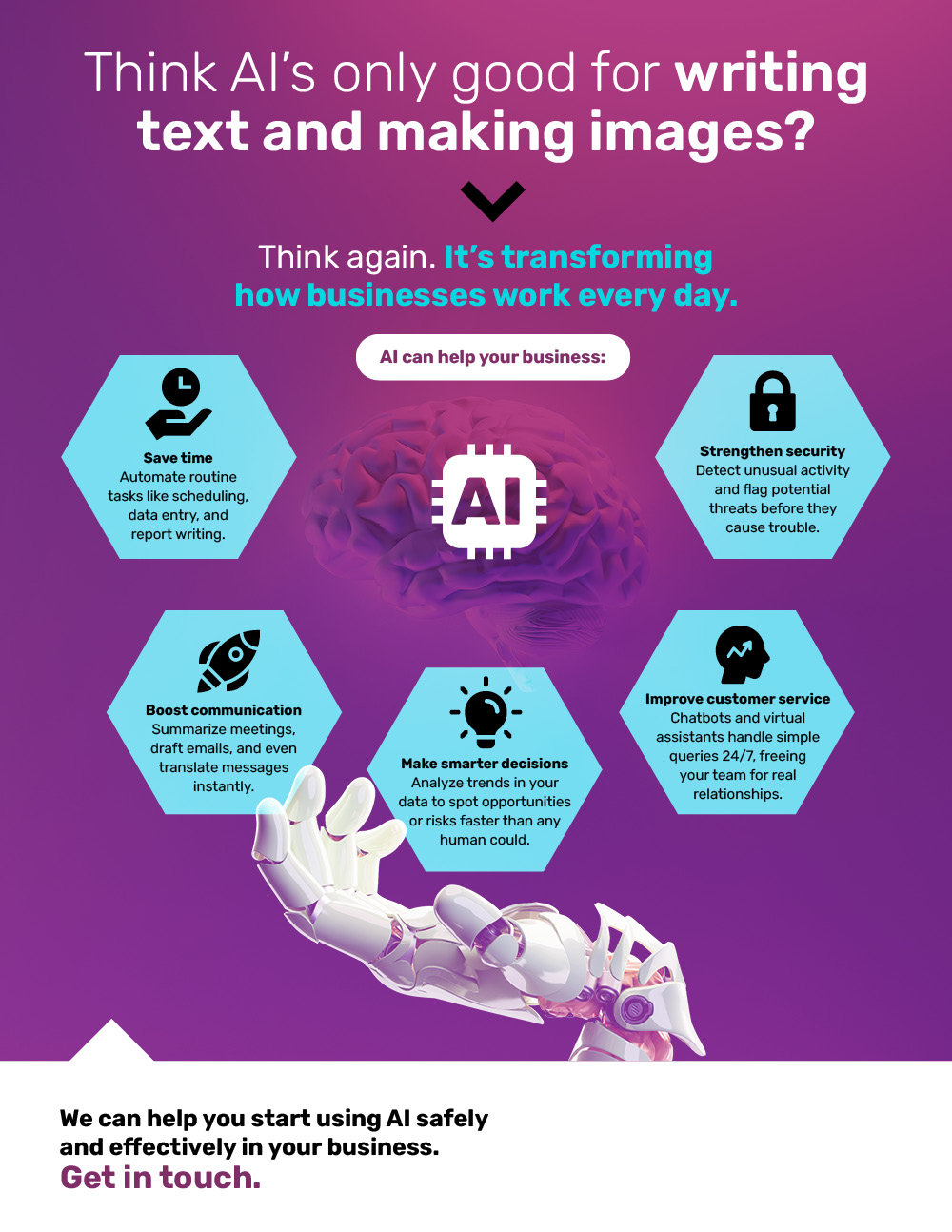
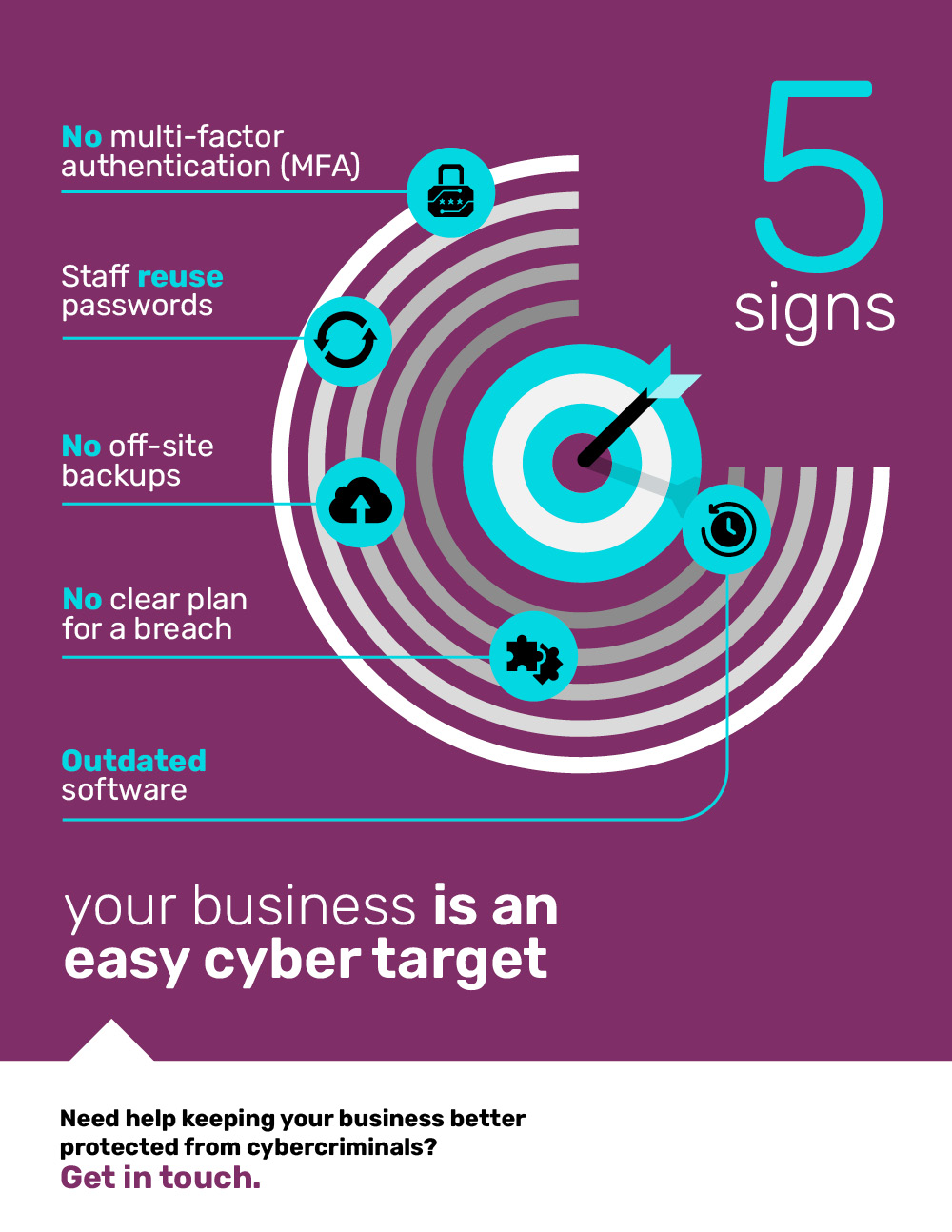
Multifactor authentication (MFA) works by requiring users to provide more than one form of identification when logging into a system or account. This extra layer of security is meant to prevent unauthorized access and protect sensitive information. However, while MFA may seem like a foolproof solution, it actually has its own set of vulnerabilities that can be exploited by cybercriminals.
The hidden weaknesses of multifactor authentication